Initial disclaimer: please check the link below, as it will be necessary when following along the pdf.
Hi, again! Ready for some more low-level code goodness?
Today we'll take a look at some very simple, yet purposefully flawed C programs in order to learn a bit more about buffer overflows, grasping control of the return address and disrupting a program's flow.
In the first example, we'll see that the program will result in a segmentation fault, and understand why that's happening exactly, by looking at the disassembled code under the GDB debugger. We'll then talk a little about registers, the return address, its importance, and how to grab control of it.
In the second example, we'll take a look at the basics, which will let us finally take advantage of the return address through a buffer overflow.
But, without much ado, let's jump to our first example. Remember that these two first programs are directly taken from Smashing The Stack For Fun And Profit, which you can find here (revised edition! - please follow this link to disable defenses. Alternatively check this. If you don't do this, you won't be able to take advantage of these methods).
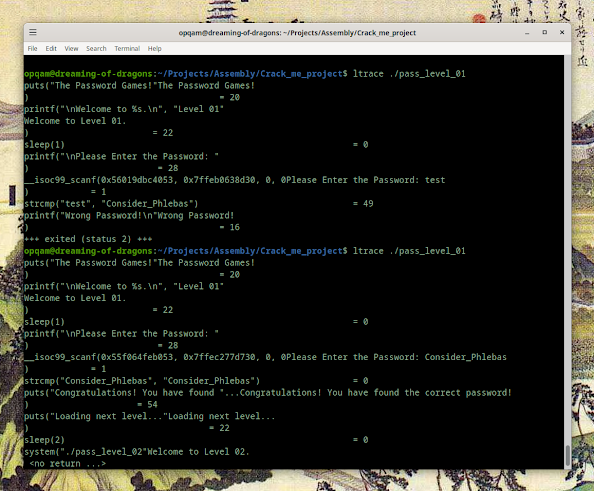
This program is creating a char array named large_string which can take up to 256 characters, and then it's filling large_string with A's. After that's done, the program is calling a function named function, using large_string as the argument. The problem becomes immediately obvious since, as we can see, inside that function, we're filling a char array entitled buffer with our A's. But our buffer can only take in 16 characters.
Ergo, we have our buffer overflow.
Function was created and its local variable buffer can only hold so many of our A's. But, since we're using strcpy, which has no control for how many values we can enter, we'll just keep on writing A's until we reach the null character (at the end of large_string).
But let's open our debugger and actually see what's happening here.
So, we're looking at main(). Can you see our loop? We're moving 'A' into eax and advancing the counter at ebp-12. A is the ASCII representation of number 41:
0x000011ea <+50>: mov BYTE PTR [eax],0x41
Adding +1 to our counter at ebp-0cx:
0x000011ed <+53>: add DWORD PTR [ebp-0xc],0x1
And comparing that value with 254 (so as to know when to end the loop):
0x000011f1 <+57>: cmp DWORD PTR [ebp-0xc],0xfe
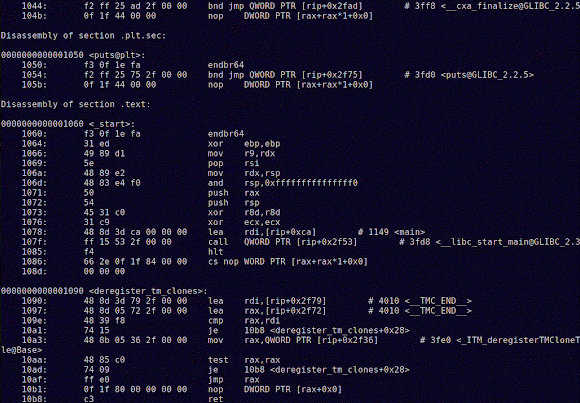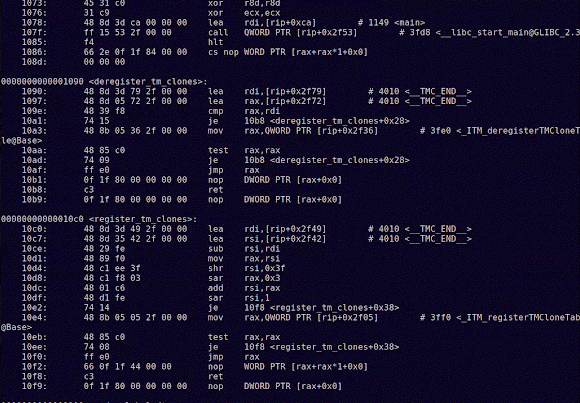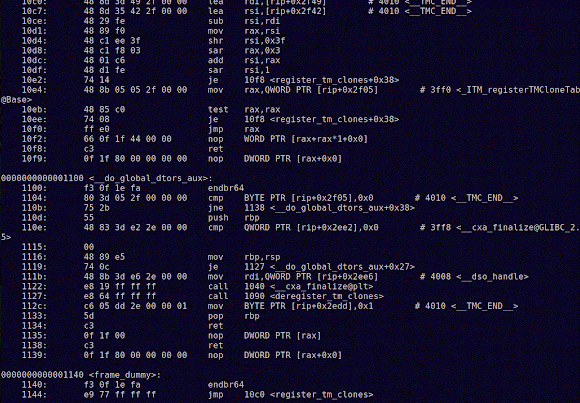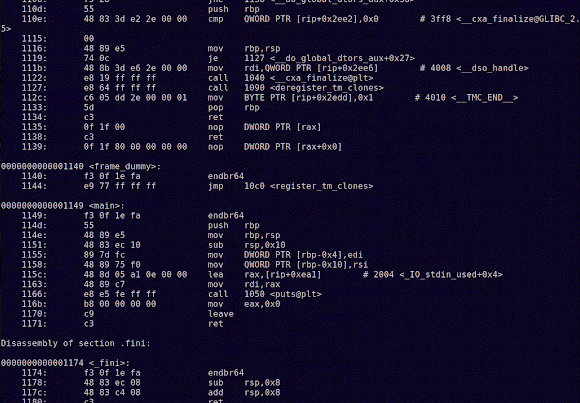
When this is finally done, as I'm sure you can see, we're jumping right into our function, and this is where the fun starts. Let's disassemble it:
Please take a moment to learn what's happening here, and compare it side by side with the C code. But let us move on and actually see what's happening with our memory, as we set a breakpoint in main:
With x/32x $esp, we're checking memory position 0xffffcfa0, to which ESP is pointing, and the addresses 32 bytes above that. I won't go into much detail. You'll see soon enough what will happen when we step forward and finally reach our function breakpoint:
Looking at the memory addresses, it's obvious what happened: these locations were filled with 0x41414141 or, in plain text, AAAA.
It's important to note that the A's are being written from higher memory positions to lower ones. This is crucial because one of the last things overwritten is the return address, which will cause our segmentation fault.
As we move along, at a certain point, the return address will also be filled with A's, and at that moment we won't have a valid return address any longer. As a result, our program will suffer a segmentation fault.
And that's it. We're going nowhere fast. This program has just died on our hands.
If we were trying to crack this program, we would have wanted, instead, to take control of the return address stored next to EBP. We'd use that value and point towards some other function we wanted, for example, thus altering the program's flow in our favor.
Yes, we're slowly creeping towards true shellcode. We'll get there eventually, don't worry.
But before we do that, we might as well talk about other interesting tidbits that can prove helpful when using a debugger and watching our shellcode or buffer overflow in action.
I've already shown quite a few pics, so I won't give you another one, but here's the very first function that appears in our "Smashing the Stack" doc. It's pretty simple, but it hopefully shines a light on the function we've been analyzing so far:
void function(int a, int b, int c) {
char buffer1[5];
char buffer2[10];
}
void main() {
function(1,2,3);
}
If we look at the memory locations, as we did before with the other program, we'll see:
0xffffd09c: 0x00000000 0xf7ffcff4 0x0000002c 0x00000000
0xffffd0ac: 0xffffdfc0 0xf7fc7550 0x00000000 0xf7da2a4f
0xffffd0bc: 0xffffd0e8 0x565561e5 0x00000001 0x00000002
0xffffd0cc: 0x00000003 0xffffd110 0xf7fc1688 0xf7fc1b60
0xffffd0dc: 0x00000000 0xffffd100 0xf7fa2ff4 0x00000000
0xffffd0ec: 0xf7da92d5 0x00000000 0x00000070 0xf7ffcff4
0xffffd0fc: 0xf7da92d5 0x00000001 0xffffd1b4 0xffffd1bc
0xffffd10c: 0xffffd120 0xf7fa2ff4 0x565561b6 0x00000001
I have put in bold important addresses and their contents. In order, from left to right, going down...
ESP
- Points to the current top of the stack.
At 0xffffd09c (the lowest memory address in this snapshot)- ESP is showing the exact spot in memory where new data are pushed onto the stack
Saved EBP
- At 0xffffd0bc
- The base pointer of the caller function
- This marks the base of the previous stack frame before the current function was called
Return Address
- At 0xffffd0c0
- This is the address the program will jump back to after the current function completes
- overwriting this location with a malicious address can cause the program to "return" to an arbitrary memory location
Variables
- Just below the saved EBP and return address are the local variables and parameters
- At 0xffffd0c4 (
0x00000001), 0xffffd0c8 (0x00000002) and 0xffffd0cc (0x00000003)
Buffer
- Just below these local variables we can see the space that has been assigned to our buffer1 and buffer2 local variables
- It's not 5+10 bytes in size. Instead, because of padding and alignment, it will be 8+12 bytes in size, for a total of 20 bytes.
Next up: We'll learn how to control the return address and force the program to do our bidding. This will set the stage for mastering the art of shellcoding!






































.jpg)


