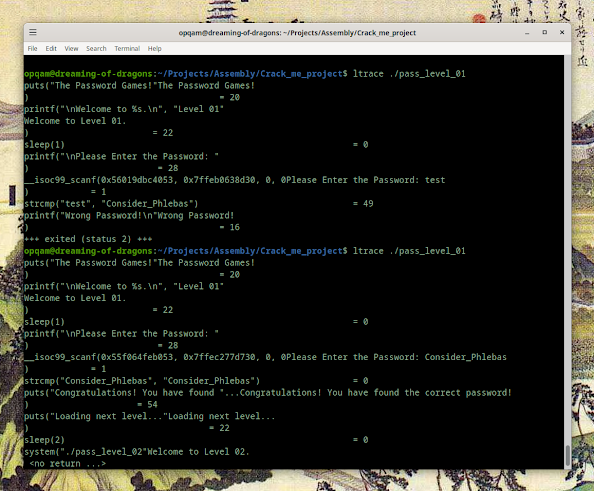
Here are some useful commands and tips that will help you navigate and debug your programs efficiently:
GDB Debugger Quick Reference Guide
Essential GDB Commands
Program Control
break [breakpoint] - Set a breakpoint
- Example:
break main, break *0x4004a0
- Tip: Use
break file.c:42 to break at specific source lines
run [args] - Start program with optional argumentscontinue (c) - Continue executionnext (n) - Step over function callsstep (s) - Step into function callsstepi - Step one assembly instructionfinish - Run until current function returns
break [breakpoint] - Set a breakpoint
- Example:
break main,break *0x4004a0 - Tip: Use
break file.c:42to break at specific source lines
run [args] - Start program with optional argumentscontinue (c) - Continue executionnext (n) - Step over function callsstep (s) - Step into function callsstepi - Step one assembly instructionfinish - Run until current function returnsInspection
print [expression] - Print value
- Example:
print x, print *ptr, print $eax
display [expression] - Auto-print at each stopx/[n][f][u] [address] - Examine memory
- n: Number of units to display
- f: Format (x=hex, d=decimal, s=string)
- u: Unit size (b=byte, h=halfword, w=word, g=giant)
- Example:
x/32xb $esp - Show 32 bytes at stack pointer
info registers - Show register valuesbt [full] - Show backtrace (call stack)
print [expression] - Print value
- Example:
print x,print *ptr,print $eax
display [expression] - Auto-print at each stopx/[n][f][u] [address] - Examine memory
- n: Number of units to display
- f: Format (x=hex, d=decimal, s=string)
- u: Unit size (b=byte, h=halfword, w=word, g=giant)
- Example:
x/32xb $esp- Show 32 bytes at stack pointer
info registers - Show register valuesbt [full] - Show backtrace (call stack)Interface
layout asm - Show assembly viewlayout src - Show source code viewlayout regs - Show registers viewlayout split - Split view (source/assembly)focus cmd/src/asm/regs - Switch between viewsrefresh - Refresh screen
layout asm - Show assembly viewlayout src - Show source code viewlayout regs - Show registers viewlayout split - Split view (source/assembly)focus cmd/src/asm/regs - Switch between viewsrefresh - Refresh screenData & Variables
info locals - Show local variablesinfo args - Show function argumentswatch [expression] - Break on value changeset variable [name]=[value] - Modify variablewhatis [variable] - Show variable type
info locals - Show local variablesinfo args - Show function argumentswatch [expression] - Break on value changeset variable [name]=[value] - Modify variablewhatis [variable] - Show variable typeCompilation for Debugging
gcc -g -O0 program.c -o program
gcc -g -O0 program.c -o programKey flags:
-g- Include debug symbols-O0- Disable optimization-fno-stack-protector- Disable stack protection-no-pie- Disable position-independent code-m32- Force 32-bit compilation
Advanced Features
Core Dumps
# Enable core dumps
ulimit -c unlimited
# Load core dump
gdb ./program core
# Enable core dumps
ulimit -c unlimited
# Load core dump
gdb ./program coreASLR Control
# Disable ASLR for debugging
echo 0 | sudo tee /proc/sys/kernel/randomize_va_space
# Or temporarily:
setarch `uname -m` -R ./program
# Disable ASLR for debugging
echo 0 | sudo tee /proc/sys/kernel/randomize_va_space
# Or temporarily:
setarch `uname -m` -R ./programRemote Debugging
# On target machine
gdbserver :2345 ./program
# On host machine
gdb
(gdb) target remote target_ip:2345
# On target machine
gdbserver :2345 ./program
# On host machine
gdb
(gdb) target remote target_ip:2345Tips for Effective Debugging
- Use conditional breakpoints:
break main if argc > 1
- Save common commands in
.gdbinit:set disassembly-flavor intel
set history save on
set print pretty on
- Create command aliases:
define reg
info registers
end
- Use Python scripting for complex debugging:
python
class MyCommand(gdb.Command):
def __init__(self):
super(MyCommand, self).__init__("mycommand", gdb.COMMAND_USER)
MyCommand()
end
break main if argc > 1
.gdbinit:set disassembly-flavor intel set history save on set print pretty on
define reg info registers end
python class MyCommand(gdb.Command): def __init__(self): super(MyCommand, self).__init__("mycommand", gdb.COMMAND_USER) MyCommand() end
I think that these commands will serve you well in your journey with a debugger.
If you have any questions, doubts or ideas to improve this list, just send them my way.
Enjoy!









.jpg)